Introduction to ControlLogix Security
In this section, we’ll discuss the topic of ControlLogix Security. This post will not go in depth. However, we will discuss some simple things you can do. Today much of the industry is a target for cyber attacks. For this reason, you will want to think about locking down your projects. It’s important to realize though, there needs to be some balance. In other words, you don’t want to security to interfere with production. Furthermore, when a technician needs to get into a project for maintenance, security should not be much of a hindrance.
Add a Password for ControlLogix Security
You have the ability to use the Logix CPU Security Tool. This allows you to password protect your processor. Access this from the “Tools” menu in Studio 5000. Simply Browse for your project, and click “Secure Controller”.
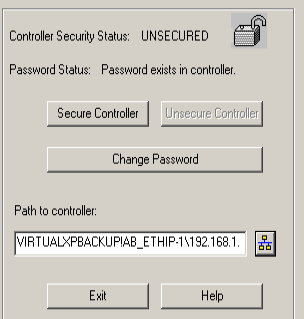
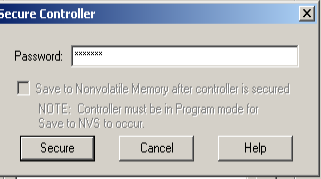
At this point, enter a password. Press “Secure”, then “Exit”. If you were online, you will be taken offline.
After that, anyone who tries to go online will get this message:
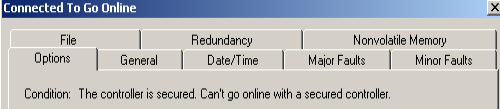
They must run the security tool again to unlock the controller. As I have said before, we don’t want this to be a hindrance to other technicians. Be sure that anyone who needs to get into the logic program knows the password. Additionally, be sure they are also familiar with this security tool.
Isolate your Control System
For the most part, control systems should not have a direct path to the Internet. Be sure your control system is on it’s own Ethernet Switch. When a technician needs to go online, they simply disconnect from your main plant network, and plug into the control network. Be sure they understand how to change the IP address of their laptop. Also, ensure they are familiar with how the subnet mask works. This will ensure they are in the same subnet as your control networks.
If your control system must connect to computers that have access to the Internet, then be sure you have a team that knows how to configure network security properly.
Make Backups
Anytime you make a change, be sure to create a new backup. It’s also a good idea to create a history of backups. In this case, just click “File Save As”. Append the name of your backup file with the date. That way, you always know what the latest version is. Always keep multiple copies of your backups in different locations. You don’t want a disgruntled employee to crash the processor, and destroy the backups.
Be Careful of Vendors
For the most part, most vendors are good. It’s important to realize though that your employees need access to the ControlLogix code. There are vendors who lock down their code so no one can see it. Sometimes no one else can even go online with the processor. They might do this in the name of security. Additionally, they might do this in the name of IP protection.
The problem with this is that you will need to invite the vendor into your plant to make even the simplest changes to the program. Alone, this presents some security risk. In the worst case, since the code is not open to see, they could have planted a “time bomb” in the code. That is code that causes your equipment to become erratic after a certain amount of time. It’s possible that they could use this deception to generate revenue. When you can openly view the code, this type of deception is nearly impossible.
Change Management
Another option is to use change management software. Rockwell has software called “RSMACC”. This has the ability to manage any changes in your controller’s software. Even simple changes can cause problems in your machine operation. For example, you might make a change to maximize production. However, the person doing the change didn’t take into account how those changes affect other modes of operation. If you have a log of the changes, it’s easy to review, and correct the offending code.
Summary of ControlLogix Security
In short, be sure no one can hack into your system from the Internet. Also, be aware of closed source programs. When purchasing equipment, be sure it’s in the contract that you have full access to the source code. Keep backups at multiple locations, and be sure everyone understands how to access your systems when they need to. These are just some of the precautions you can take. It’s important to realize though that no system is entirely 100% secure. With a few steps, though, you will greatly minimize your risks.
For more information, visit other ControlLogix Posts!
— Ricky Bryce
